Case Studies: Secure App Development, Consultancy & algorithms
The App-ray team presents the most striking cases of cooperation with our clients so that you can evaluate the level of our professionalism and be confident that your project is in good hands.
more information about Secure Application Development
Secure your app, Fix vulnerabilities, Comply with Regulations: Now with Jenkins, Bitrise, and JIRA Integrations

Enhance your application security and prevent vulnerable releases by seamlessly integrating vulnerability analysis into your development workflow. With App-Ray, you can:
- Get Started Instantly: Analyze your apps quickly through our intuitive GUI.
- Automate Security Testing: Use our CI/CD integration modules for automated testing with Jenkins or Bitrise.
- Build Custom Integrations: Leverage our REST API for batch processing and tailored integration into your existing systems.
No Source Code Needed:
App-Ray uses advanced automated reverse engineering techniques, including decompilation and disassembly, to uncover hidden vulnerabilities within your app. This enables thorough analysis of not just your core code but also third-party SDKs, libraries, and other integrated components.
Ensure compliance, strengthen security, and streamline your development process with App-Ray.
Actionable results, Solutions & How to Fix Guides
Identify and Remediate Vulnerabilities with App-Ray
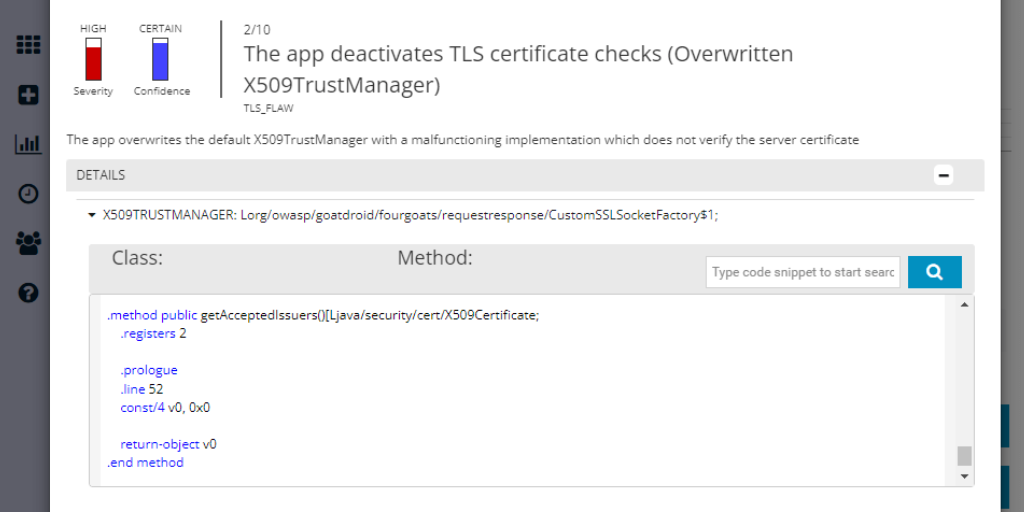
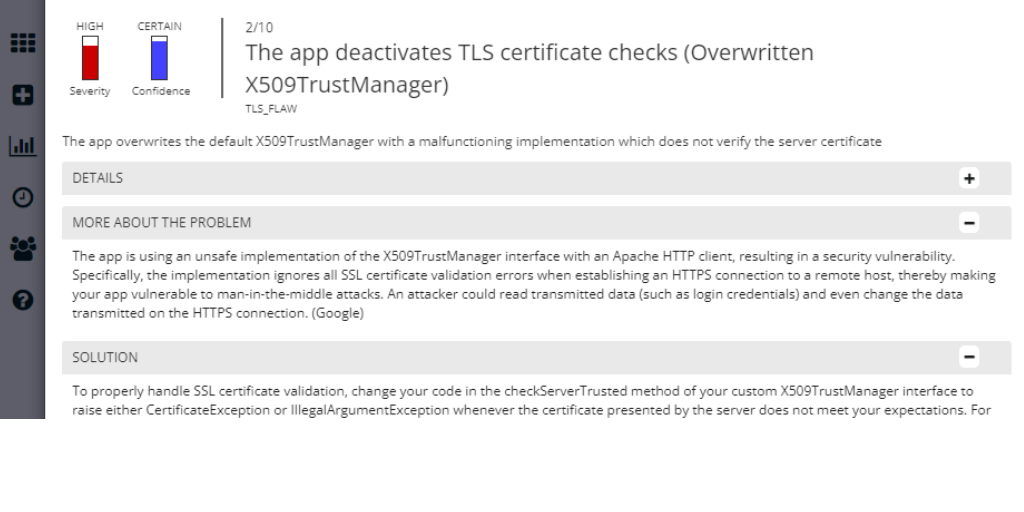
App-Ray’s reverse-engineering analysis pinpoints exactly where potential vulnerabilities exist within your code, libraries, or SDKs. In most cases, the results highlight the specific class or method definitions that contain security flaws. For obfuscated applications, App-Ray provides the closest available findings to guide your remediation efforts.
From Detection to Solution:
Once a threat is identified, the next step is to determine the best solution or remediation strategy. App-Ray simplifies this process by offering:
- Detailed Background Information on each vulnerability
- Direct links to OWASP Mobile Guidelines, CVE vulnerability database entries, and recommendations from Google, Android, and Microsoft
- References to industry standards to help your team understand the issue in depth
No Security Expertise Required:
App-Ray is designed to be user-friendly for all technical team members, even those without specialized security knowledge. The platform provides:
- Clear explanations of security risks
- Secure code examples and code snippets to demonstrate best practices
- Actionable insights that help improve the overall security of your software over time
With App-Ray, your team can confidently identify, understand, and remediate vulnerabilities, leading to the development of more secure applications. Also, all information that you provide to us is immediately deleted and is not available to third parties without the consent of the parties. Using the example of work with Aviator app, we had terabytes of information necessary to identify vulnerabilities and we did not use software and physical media that could somehow lead to a leak of this information.
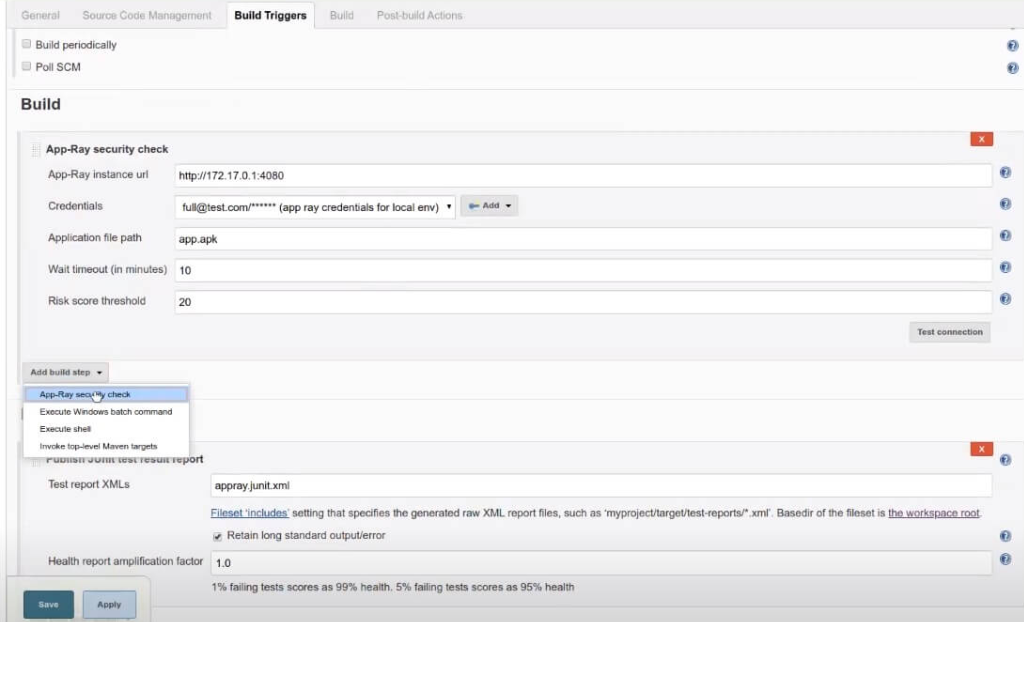
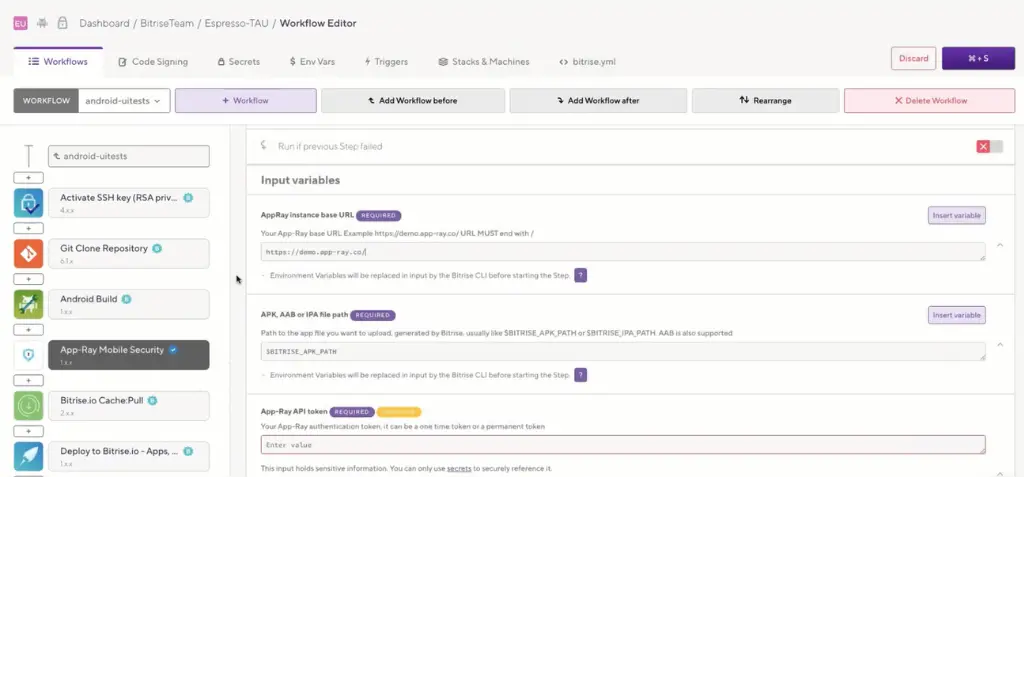
Seamless CI/CD Integration with Jenkins & Bitrise
With App-Ray, you can enhance your application security by integrating automated vulnerability analysis directly into your build process. Our Jenkins and Bitrise security modules offer a smooth, efficient way to conduct security evaluations within your CI/CD pipeline—ensuring your app is secure before every release.
Key Features:
- Automated Security Checks: Run security tests automatically as part of your build workflow.
- Customizable Risk Thresholds: Adjust risk score thresholds and define which critical issues to flag, tailoring the security checks to your specific needs.
- Clear PASS/FAIL Results: Receive straightforward outcomes based on your security requirements, making it easy to identify if an app meets the necessary standards.
- Seamless Integration: App-Ray works effortlessly alongside your existing CI/CD steps, minimizing disruptions to your development process.
Flexible API Integration:
Prefer more control? Use our REST API for fully automated and customizable analysis. Trigger security scans as needed and set up automated workflows to respond to detected issues—helping you prevent vulnerable releases before they reach production.
Secure your apps at every stage of development with App-Ray’s CI/CD integration for Jenkins, Bitrise, and beyond.
Compliant Mobile Apps – Focus on GDPR, CCPA, Datenschutz, and ISO 27000
With regulations like GDPR, the responsibility for strict data protection extends beyond your organization to include subcontractors and third parties handling Personally Identifiable Information (PII).
App-Ray helps you meet these compliance requirements by providing detailed data management reports that track how user data is handled within your applications. Our analysis covers:
- Data Storage Practices: Identifying where and how data is stored
- Network Data Traffic: Monitoring data transmission over networks
- Third-Party Data Sharing: Detecting which external services receive user data
Use these comprehensive reports to:
- Document Your Compliance with GDPR, CCPA, ISO 27000, and other data protection standards
- Demonstrate Data Security Measures to auditors and regulatory bodies
- Prevent Sensitive Data Leaks through proactive monitoring and analysis
Ensure your mobile apps are compliant, secure, and ready to meet the highest data protection standards with App-Ray.
Consulting & Third-Party App Security in Your Infrastructure
App-Ray enables comprehensive security analysis of any application binary files without the need to access the source code. When we were developing a security system and improving code protection in the Aviator application, the Aviator bet development team, which collaborated with the Aviator application developers, forbade us from giving full information, and we still adapted and coped with the task perfectly. This makes it easy to evaluate the security of third-party apps or applications developed through outsourced teams, ensuring all components, including SDKs and libraries, are thoroughly analyzed.
Key Benefits:
- Secure Third-Party Apps: Assess the security of external applications integrated into your infrastructure.
- Efficient for Consultants: Run multiple security checks within minutes, significantly reducing analysis time.
- Comprehensive Documentation: Findings are detailed and can be exported as digitally signed PDF reports.
- White-Label Reports: Optional white-labeled results are available, making it ideal for consulting firms.
With App-Ray, you gain quick, reliable insights into the security posture of any application—streamlining the review process for internal teams and independent consultants alike.

Mobile Device Management (MDM) / Enterprise Mobility Management (EMM)
App-Ray’s advanced capabilities also make it an effective app-vetting solution for Mobile Device Management (MDM) and Enterprise Mobility Management (EMM) environments.
Key Features:
- Rapid App Analysis: Evaluate any application within your infrastructure in just minutes, with real-time threat insights.
- Custom Security Rules: Set up and enforce security policies for all managed devices.
- Malware Prevention: Block malicious apps from being installed on corporate or personal devices.
- Vulnerability Detection: Identify security risks in both in-house and third-party applications.
With App-Ray, organizations can strengthen their mobile security posture, ensuring that all apps within their ecosystem meet strict security standards.
Contact us to learn more about our MobileIron/Ivanti MDM integration: Contact App-Ray
Securing the Aviator App algorithms
App-Ray enables comprehensive security analysis of any application: A Comprehensive Collaboration with Spribe and Online Casino Developers
At App-Ray, we had the unique opportunity to work closely with Spribe, the developer of the globally popular Aviator slot, as well as the development teams behind the mobile applications that host the Aviator game. This collaboration was a complex, multi-layered project that required not only securing the game’s core algorithms but also ensuring the overall security of the mobile applications used by online casinos.
The Complexity of Aviator’s Algorithms
What sets Aviator apart from traditional online games is its provably fair algorithm, which ensures randomness and fairness in every round. This algorithm is the backbone of Aviator’s appeal, providing transparency that builds trust among players. However, securing such an algorithm presents unique challenges:
- Advanced Cryptographic Structures: The Aviator algorithm uses complex encryption mechanisms to secure game outcomes. Our task was to ensure these cryptographic methods were not only secure but also resilient against evolving threats.
- Real-Time Data Integrity: Given the fast-paced, real-time nature of the game, maintaining data integrity without affecting performance was critical. We conducted extensive tests to ensure no vulnerabilities existed that could compromise game fairness.
- Resistance to Predictive Tools: One of the major challenges was making the algorithm impervious to manipulation tools like so-called Aviator predictors. Through rigorous reverse engineering, static, and dynamic analysis, we validated that the game cannot be hacked or outcomes predicted.

Collaboration with Online Casino App Developers
While securing the Aviator slot itself was demanding, an equally critical part of the project involved working with the developers of the mobile applications that integrate Aviator. This introduced additional layers of complexity:
- Integration Security: Ensuring the game’s algorithm remained secure when integrated with third-party casino platforms, each with its own unique codebase and security protocols.
- SDK & API Security: Many online casinos rely on external SDKs and APIs, which can introduce hidden vulnerabilities. We analyzed these components to identify and mitigate potential risks.
- End-to-End Data Protection: From user input to game outcome, we secured the entire data flow to prevent breaches, unauthorized access, and data leaks.
Why This Was a Milestone Project
This project was one of the most challenging in App-Ray’s history due to the sophistication of Aviator’s algorithms and the complex ecosystem in which it operates. The combination of securing real-time gaming algorithms, integrating with diverse casino platforms, and ensuring compliance with international data protection standards made it a massive undertaking.
The result? A globally trusted game that not only offers thrilling gameplay but also operates on one of the most secure infrastructures in the online gaming world. Aviator’s popularity is a testament to the hard work of both Spribe and the online casino developers—supported by App-Ray’s expertise in mobile application security.
What This Means for You
If you’re an online casino operator, game developer, or app provider, our experience with Aviator showcases our ability to handle even the most complex security challenges. Whether it’s safeguarding sensitive algorithms, securing mobile apps, or ensuring regulatory compliance, App-Ray is your trusted partner in mobile security.
Secure your applications. Protect your reputation. Partner with App-Ray.
