App-Ray Features How it works
Identify vulnerabilities, mitigate risks, comply with regulations
App-Ray static analysis (SAST) and dynamic analysis (DAST) provide actionable results with over 80 types of security vulnerabilities, data management and privacy issues to identify, for example:
- Privacy leak, user data leak, permission leak – using data flow and network traffic analysis
- Vulnerable SDKs, libraries or containing phone viruses, malware, trojans
- Insecure network communication, incorrect SSL – TLS security settings
- Encryption related issues, insufficient cryptography
- Insecure data storage, local database – SQL injection issues
- Mixed apps related issues (Insecure WebView, Webview hijacking and more)
The last point is the most difficult to ensure security when the project is cross-platform or has the same algorithm for both versions and applications, as in Aviator Demo. You can check the security we provide by simply testing the application and the Aviator demo version (on our or offitial website) at the same time and we give a 100% guarantee that you will not find any vulnerabilities.
The workflow consists of the following stages
Static Analysis – Static Application Security Testing, SAST
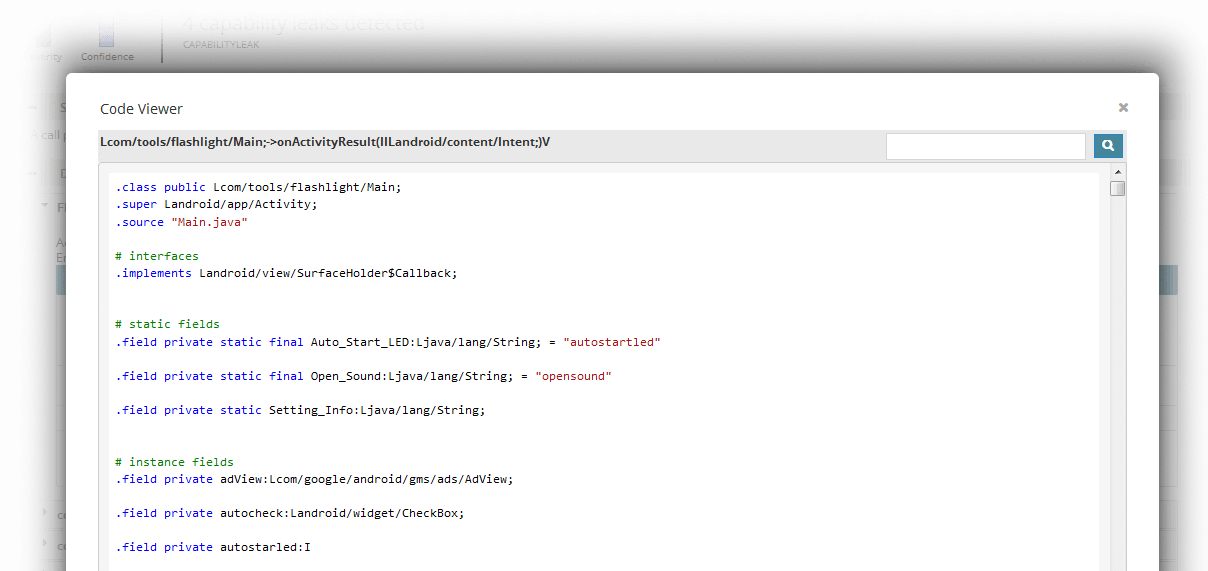
App-Ray’s static analysis uses reverse engineering – decompilation and/or disassembly – to analyze your mobile application, so access to the source code is not required. This includes examining the bytecode and structure of the application without executing it.
App-Ray has highly effective bidirectional data flow tracing, identifying unwanted data flows that may violate security and privacy requirements. This stage will identify threats to data integrity and privacy, such as SQL injections or unprotected intent.
Dynamic Analysis – Dynamic Application Security Testing, DAST
During a simple dynamic analysis, the original application is launched in a test environment and its behavior is analyzed. Screenshots are taken, network traffic is recorded, and a full trace of system calls and files accessed is created. Private information is identified and sent to advertising and user profiling platforms. Users can choose whether they want to interact with the application or the analysis will be performed completely automatically.
Want to see how App-Ray is used in production? Click here:
Instrumentation, Hybrid Analysis
Instrumentation makes a slight modification to the app to extract specific information from it in a hybrid static/dynamic analysis. Guided by knowledge gained from static analysis and modifications injected by instrumentation, App-Ray’s hybrid analysis engine investigates the app’s runtime behaviour under specific security-relevant conditions. It ensures that critical parts of the app are executed and observed.
Tracing of individual function calls and register values allow deep insights into the app’s behaviour. The hybrid engine attempts to provoke execution of vulnerable code fragments and records encrypted traffic in plaintext, allowing inspection for private information.
Reporting
App-Ray presents its most relevant findings in a structured overview. A drill-down into detailed analysis results and raw data of the analysis is possible. All analysis results are stored in App-Ray and can be retrieved at a later time in PDF, JSON formats, or via REST API for further processing. The generated reports are digitally signed, and all outputs are optionally available in White-Labelled format as well.
Test App-Ray Now
Free access to App-Ray work.
Download APK Aviator app to familiarize yourself with security methods
No commitments, no credit card required.
learn more about Apk Aviator
Want to know what App-Ray is all about?
Check out more about our work on the Aviator Game app
Contact us
Would you like to talk to us, do you have questions?
Leave us a message and your contact details, we will come back to you soon.
Subscribe to App-Ray Mobile Security
Ready to use App-Ray for production? Subscribe here quickly and conveniently.
Safe online payments, instant purchase.
